What is Cyber Security
- Cyber security is a multiple strand of technologies and practice that protect networks, devices, programs and data from receiving attacks and damages by malware, digital attacks or any access that does not have authorization
- Cyber security is a protection that protects cyber attacks ; accessing, diminishing or recasting sensitive information, extorting money from users, interrupting normal business processes
- For instance, this cyber security is alos an information technology security
Why Cyber Security important?
- Cyber Security is important as how important our daily life safeguard are
- Cyber Security is especially important for events like ; Identifying theft, extortion attempts and loss of data
- A large portion of data that are always transfering sensitively through digital network ; weather it is personal data or financial data or any type of data for which unauthorized access could end i n negative outcomes
- Therefore having a proper Cyber Security measure helps to secure your site at any cause
Do you know there are few types of Cyber Security threats?
- Ransomware – is a type of malicious software that is commonly to extort money by blocking the access or the system
- Pishing – Practice creating and sending fraud emails that represents email from reputable sources to steal credit numbers or login information
- Malware – Is a software that enables access that does not have authorization to damage the computer system
- Social engineering – is tactic to steal sensitive information by causing the party to reveal it
Be aware of DDoS attacks
- DDoS stands for Denial of Service attacks ; a malicious attempt to cause interruption on normal traffic of a targeted server, service or network by overwhelming the target with a continuous flow of internet traffic
- DDoS reaches its effectiveness by utilizing multiple compromised computer system as sources of attack traffic
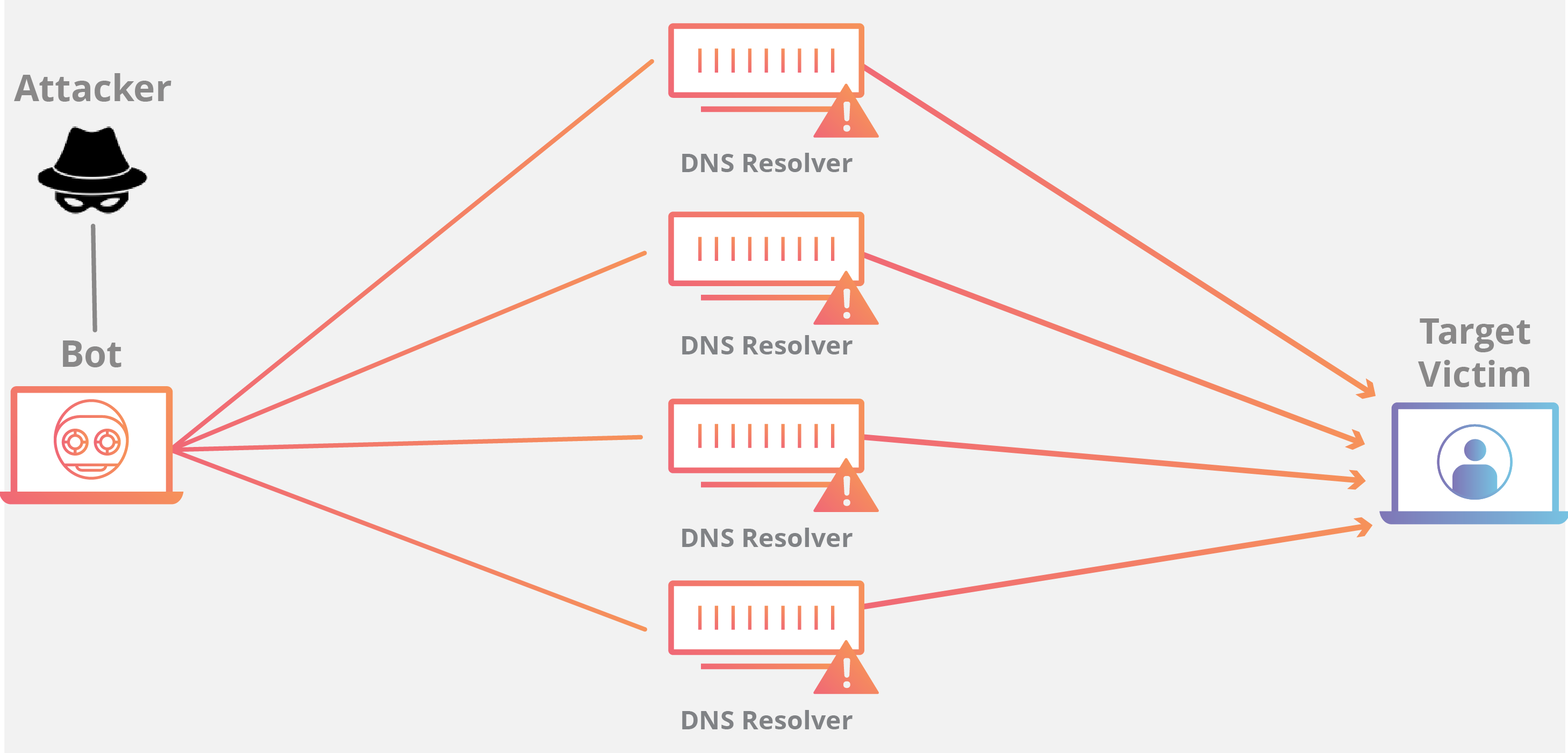
How does DDoS attack works?
- DDoS requires an attacker to obtain control of a network online in order to carry out an attack
- This causes computer and other machines being infect with malware
- The machines and computer that infects will turn into bot (zombie)
- The attacker will have remote control over the group of bots that is the botnet
- Once the botnet establishes,, the attacker is able to take over the machine by sending and structuring information to the bots
- When the IP Address targets the victim by the botnet, each bot with counter by sending requests to the target causing the targeted server to overflow capacity
- This will result on denial-of-service to normal traffic flow of the site
Common types od DDoS attacks
- Different DDoS structure target varying components of a network connection
- In order to understand how DDoS attacks, lets absorb how the network connection is made
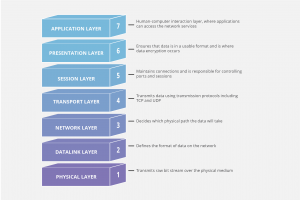
Application layer attacks
- Is called the layer 7 DDoS attack
- Layer 7 DDoS attack is mainly to expand the resources of the target
- The attacker targets the layer where web pages are generated on the server and delivered in response to HTTP requests
- Layer 7 attacks are hard to be secured as the traffic strike can be difficult to handled and it is malicious
..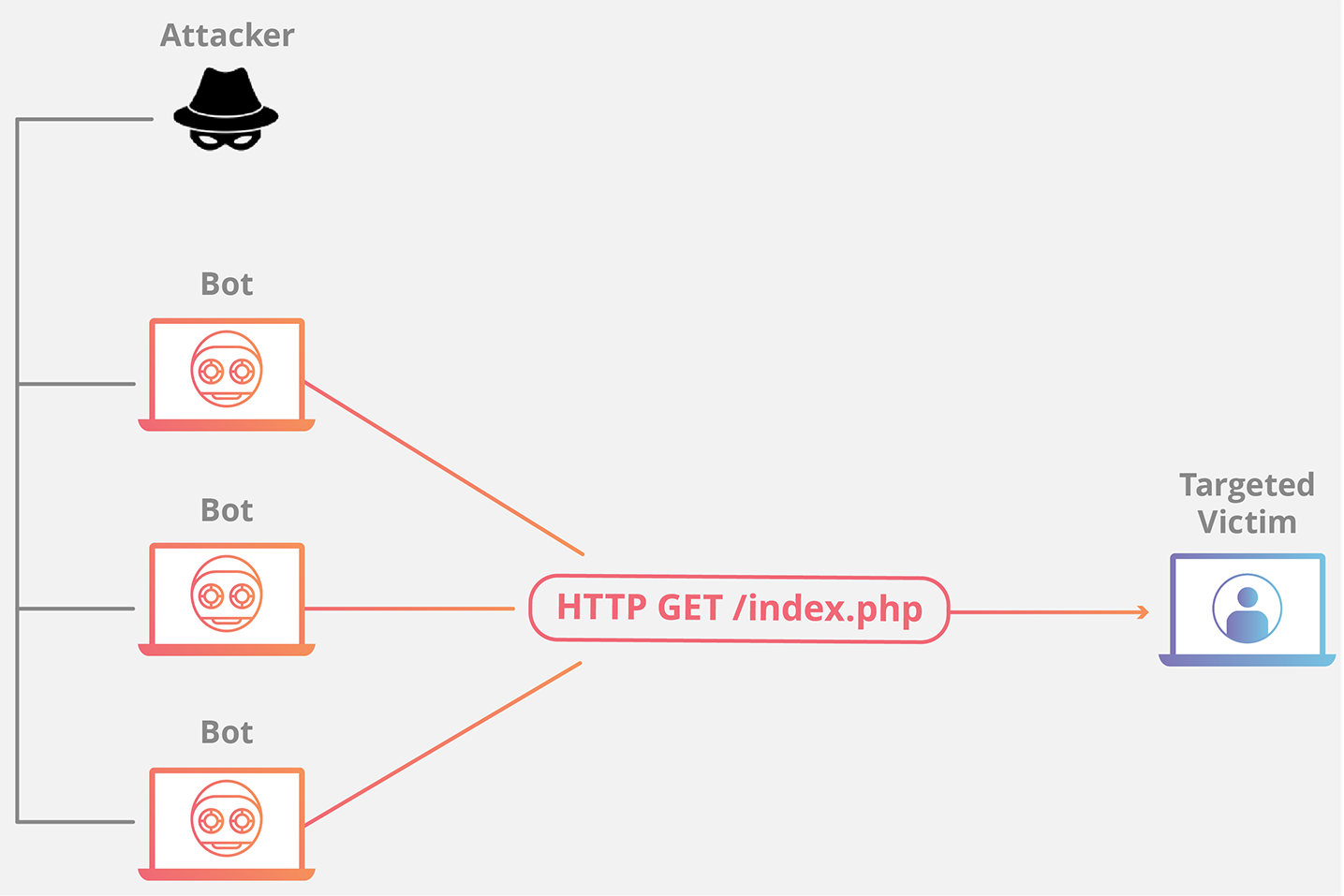
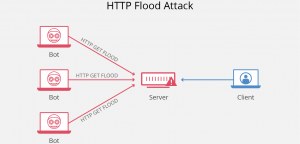
HTTP flood
- Large numbers of HTTP requests flood the server, resulting in denial-of-service
- This HTTP flood can range from simple to complex
Protocol Attacks
- Is a form of service interruption by consuming all the available state table capacity of web application servers
- This attack essentially utilizes weakness in layer 3 and 4 of the protocol stack to render the target inaccessible
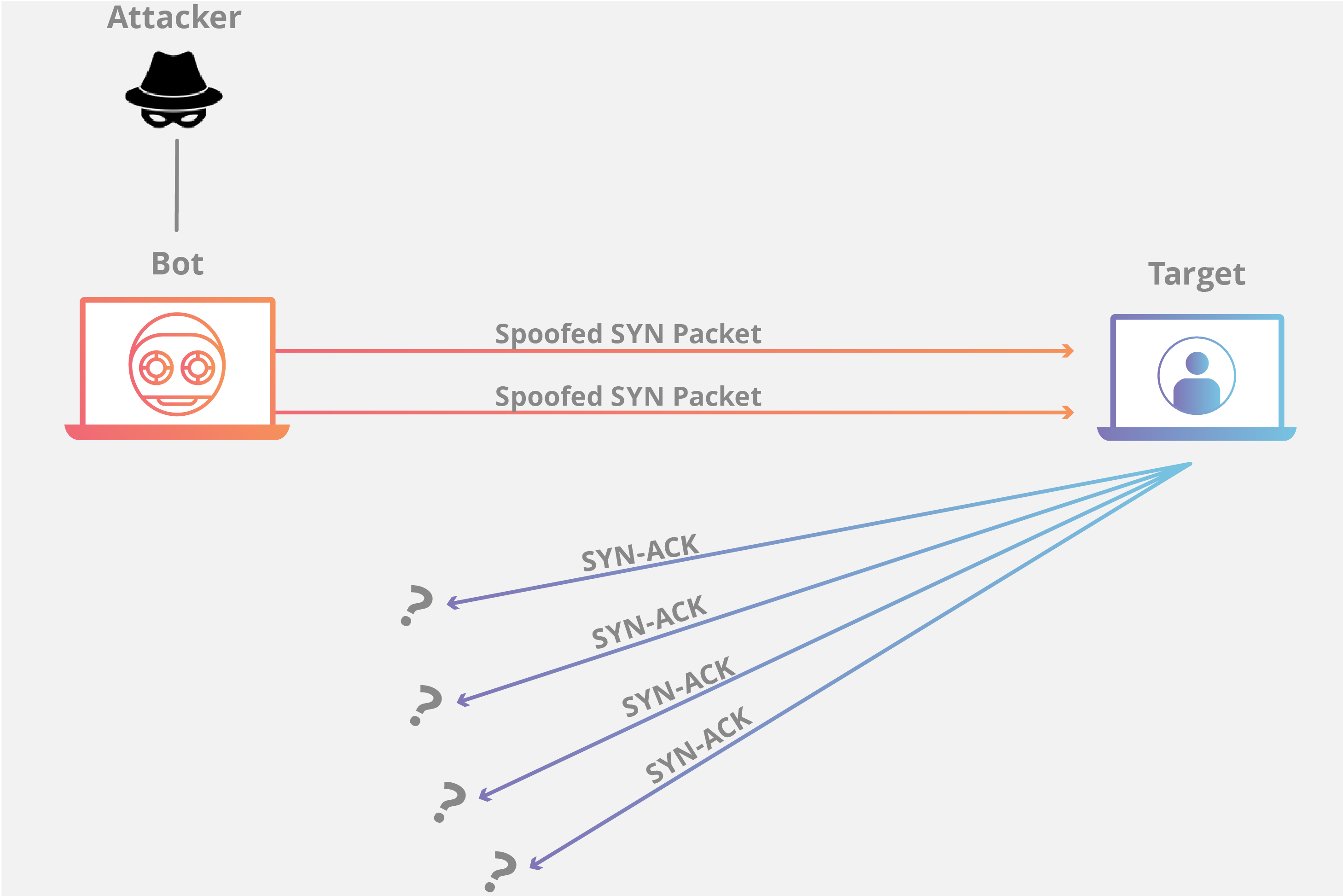
SYN Flood
- is similar to a worker from control room getting request to be answered and when it is carried on, too many requests starts to plug in the control room without confirmations and end up not answered
- This attacks particularly exploits the TCP handshake by sending a target of large number of TCP
Volumetric Attacks
- This attack is to create blockage by utilizing all available bandwidth between the target and the larger internet
- Huge amounts of data are sent to the target to create massive traffc
Mitigating DDoS Attack
- It is important to actually identify the traffic in our site is actually caused by DDoS or it is just a normal traffic
- Black Hole Routing – One solution for this is by creating a black hole route and funnel traffic into that route
- Rate Limiting – Limiting the number of requests a server will accept over a time
- Web Application Firewall – a tool that can assist mitigating a layer 7 DDoS attaclk
Need a safe and secure cyber security to run your website? Choose CasGate and you will feel the safest!
Why CasGate?
- 24/7 monitoring on DDoS pattern
- Mitigates DDos attacks within minutes
- 24/7 updates on DDoS trends
- Proffesional one-to-one consultancy provided
And many more at our Cyber security




